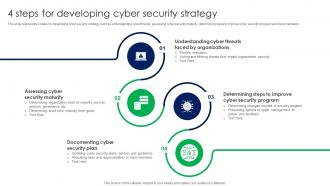
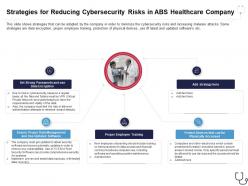
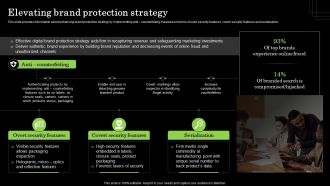
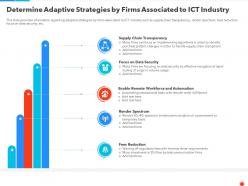
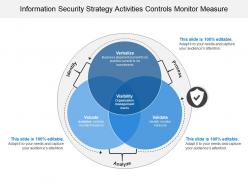
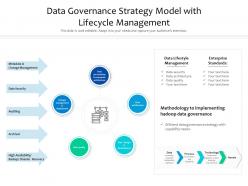
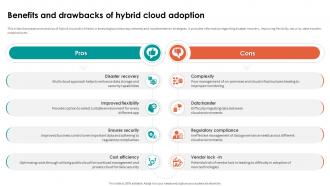
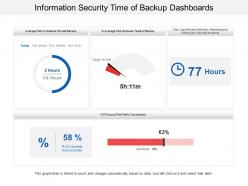
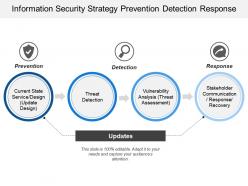
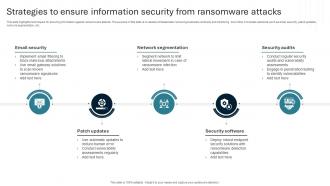
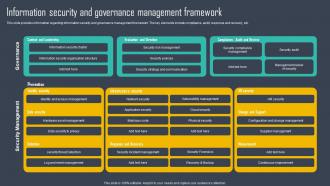
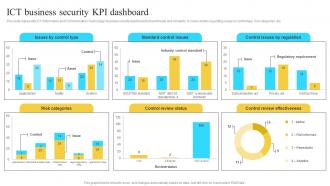
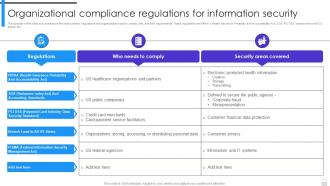
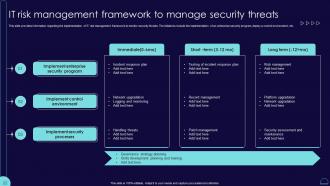
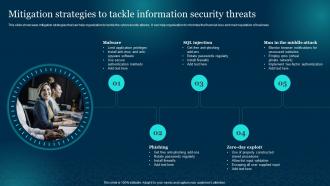
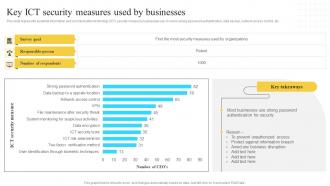
Information Security Strategy
Sort:
Refine your search
Related Categories
Governance
| Security Strategy
| Threat Mitigation
| Incident Management
| Innovation Governance
| Financial Strategy
| Partner Plan
| Cyber Incident