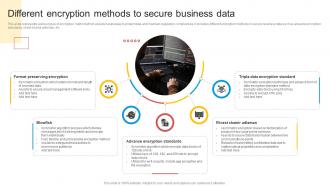
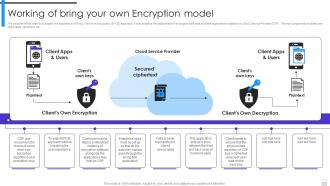
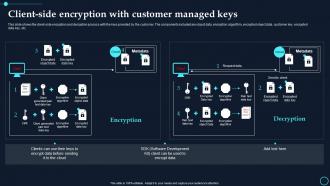
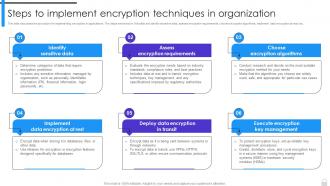
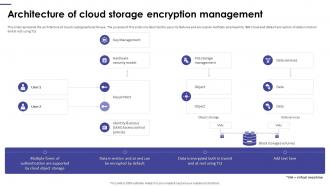
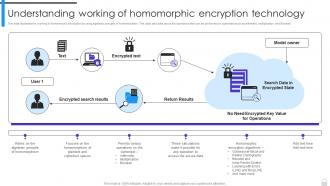
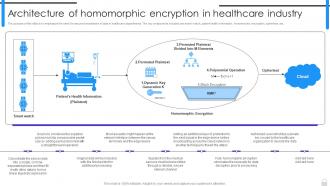
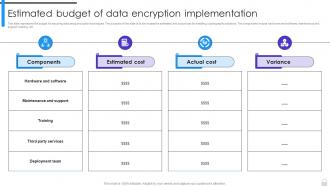
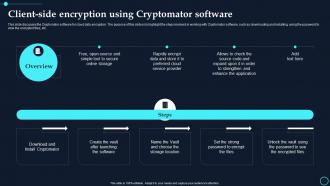
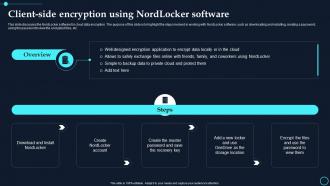
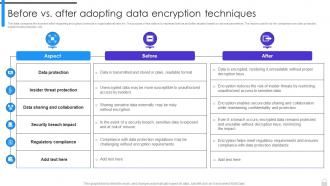
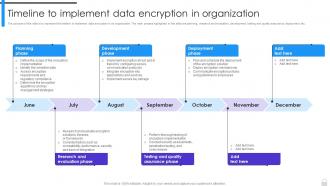
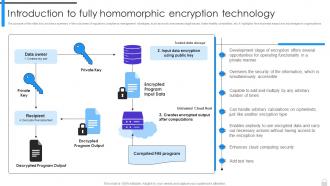
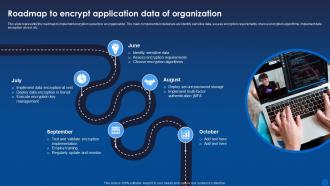
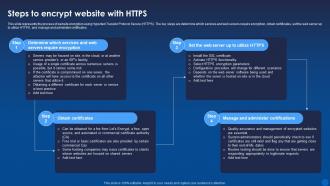
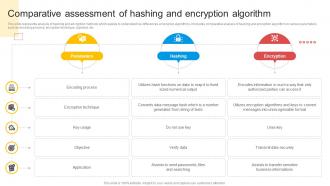
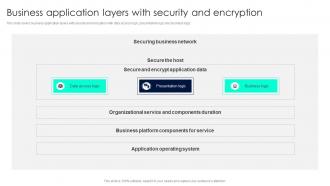
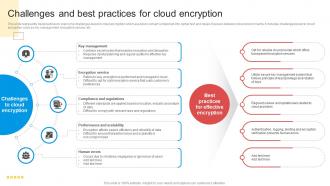
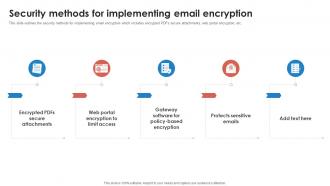
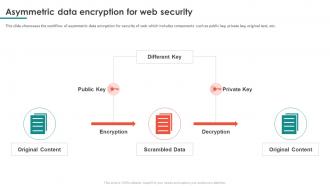
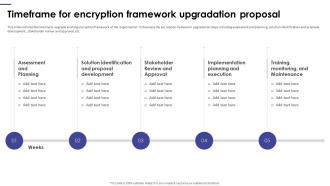
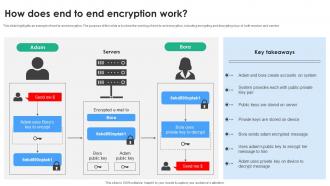
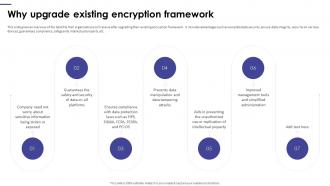
Encryption
Sort:
Refine your search
Category
- AI (13)
- Branding (8)
- Business Plans (5)
- Business Slides (1406)
- Change Management (2)
- Circular (68)
- Cluster (4)
- Complete Decks (117)
- Concepts 1 (2)
- Diagrams (1381)
- Division (1)
- Essentials 1 (91)
- Essentials 2 (25)
- Finance (4)
- Flat Designs (1396)
- Hierarchy (11)
- Icons (164)
- Illustrations (11)
- Image Slides (1)
- IOT (1)
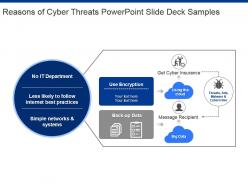
- IT (30)
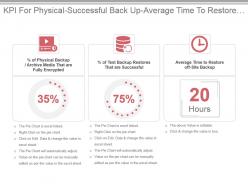
- KPIs (1)
- Layered (78)
- Linear (304)
- Management (2)
- Marketing (5)
- Medical (1)
- Medical 2 (1)
- Mini Decks (10)
- Pitch Deck (1)
- Powerpoint Backgrounds (1)
- Project Management (4)
- Proposals (1)
- Puzzles (1)
- Roadmap (2)
- StockPhotos (1)
- Strategy (4)
- Technology (4)
- Technology 1 (134)
- Technology 2 (44)
- Variety 1 (1)
- Variety 3 (2)
Related Categories
Data Analysis
| Internet Of Things
| Lock Puzzle
| Secure And Expansion
| Internal Communications Strategy
| Technology Strategy
| Block Chain
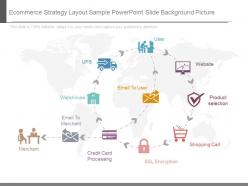
| Ecommerce Strategy